Configuring a Basic Firewall With A10 Thunder CFW
The A10 Thunder Convergent Firewall (CFW) has a large set of technologies and features. This article will describe the most basic configuration of the Thunder CFW deployed at the edge of a corporate network and connected directly to the Internet. The purpose of this document is to guide the reader in setting up a basic firewall configuration which will securely route internal network traffic to the Internet.
Lab Overview
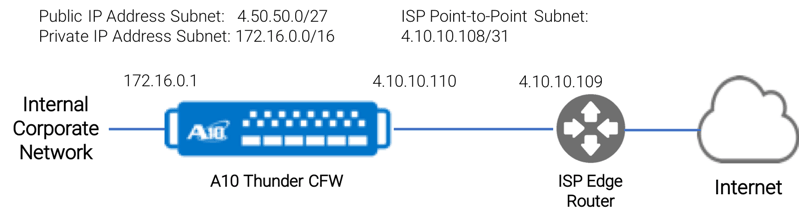
The overview for this example consists of:
- Internal Corporate Network – the private internal network
- A10 Thunder CFW – the Thunder CFW product using only the data center firewall feature sets
- ISP Point-to-Point Subnet – a typical network configuration where an ISP will provide access to the Internet via a /31 subnet which supports only 2 nodes. This link is used only to route traffic between the A10 Thunder CFW and the ISP edge network.
- Public IP Address Subnet: An IP subnet range of public IP addresses. This range allows direct access to the Internet without requiring NAT.
The most basic configuration for this network includes the following Thunder CFW technologies:
- A10 CFW Stateful Firewall feature set
- A10 Carrier Grade NAT feature
- Standard IP Routing
The following is a complete command line configuration for the A10 Thunder CFW:
class-list inside
172.20.0.0/16 lsn-lid 1
!
interface ethernet 1
name External
enable
ip address 4.10.10.110 255.255.255.252
ip nat outside
!
interface ethernet 3
name CorporateNet
enable
ip address 172.16.0.1 255.255.0.0
ip nat inside
!
ip route 0.0.0.0 /0 4.10.10.109
!
cgnv6 lsn inside source class-list inside
!
cgnv6 nat pool public 4.50.50.2 netmask /32
!
cgnv6 lsn-lid 1
source-nat-pool public
!
rule-set firewall
rule 30
action permit cgnv6
source ipv4-address any
source zone any
dest ipv4-address any
dest zone any
service any
!
fw active-rule-set firewall
!
endNAT Configuration
The following commands configure Carrier Grade NAT (CGNAT) to translate inside addresses to a public external IP address. In this case, all traffic will be exposed as a single IP address 4.50.50.2.
class-list inside
172.20.0.0/16 lsn-lid 1
cgnv6 lsn inside source class-list inside
cgnv6 nat pool public 4.50.50.2 netmask /32
cgnv6 lsn-lid 1
source-nat-pool publicFirewall Configuration
The following commands create a single firewall ruleset, which processes outgoing traffic and enables the NAT functionality using CGNAT.
rule-set firewall
rule 30
action permit cgnv6
source ipv4-address any
source zone any
dest ipv4-address any
dest zone any
service any
fw active-rule-set firewallIP Routing
IP traffic is routed through interface Ethernet 1 directly to the ISP edge router device.ip route 0.0.0.0 /0 4.10.10.109
Summary
This article described a simple firewall configuration. The purpose of this is the provide a quick start instruction to setup and troubleshoot a basic configuration. There are hundreds of features included with the A10 Thunder CFW. From this basic configuration, the customer can then customize the system, adding features one at a time.
The follow up article starts with the firewall configuration above, and shows how to add an application service to A10 Thunder CFW.
Seeing is believing.
Schedule a live demo today.